Integrating Verifiable Credentials and Decentralized Identifiers for identification and authorization in the IoT
Athens University of Economics and Business
In the SOFIE project we leverage two novel identification and authorization specifications, currently under standardization by W3C: Decentralized Identifiers, and Verifiable credentials. These two new technologies are incorporated into the Identification, Authentication, Authorization (IAA) and Privacy and Data Sovereignty (PDS) components of the SOFIE architecture, and they are implemented using the Hyperledger Indy permissioned ledger.
SOFIE is one of the first research efforts that incorporates these technologies in a standard authorization system and uses them to access IoT systems.
A Decentralized Identifier (DID) [1] is a new type of identifier that is globally unique, resolvable with high availability, and cryptographically verifiable. A DID system can be viewed as a key-value store system, where the key is the DID and the value is a DID document. DID documents can be stored in blockchains, distributed ledgers, (decentralized) P2P networks, or other systems with similar capabilities; these systems are referred to as Decentralized Identifier Registries. DID documents contain (among other information) public keys that can be used for linking a user to particular DID document (using an “authentication” method that depends on the type of the public key, which is also defined in the DID document), service endpoints, as well as auxiliary information that can be used for verifying the integrity of the document.
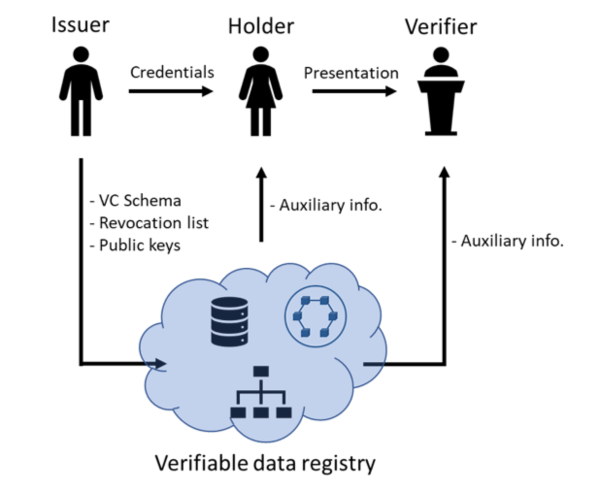
A verifiable credential (VC) [2] provides a cryptographically secure, privacy preserving, and machine-verifiable means for expressing real-world credentials in the cyber world. In contrast to standard public-key based certificates that provide a binary identification, i.e., either the whole identity of the subject is known, or nothing, VCs can be used for verifying certain attributes of a subject. VCs allow an issuer to assert one or more claims about a subject. A VC includes a set of claims, metadata that describe properties of the credential (e.g., information about the issuer), as well as a digital proof (e.g., a digital signature). A VC is issued to a holder. In most cases a subject and a holder are the same entity. A holder can prove the possession of one or more VCs to a verifier by generating a verifiable presentation. A verifiable presentation includes data from one or more verifiable credentials, packaged in such a way that the authorship of the data is verifiable. All operations are mediated by a verifiable data registry that stores relevant information such as VC schemas, revocation lists, issuers public keys, etc. A data registry can be implemented by a centralized authority or by a decentralized system, e.g., a DLT (Distributed Ledger Technology). The figure provides a high-level overview of the entities and the interactions that take place when VCs are used.
An important feature of VC is self-sovereignty, which has significant benefits, including the following [3]:
- Control: subjects have ultimate control over their claims whether self-specified or specified by others.
- Portability: Information and services about a claim are transportable.
- Interoperability: claims can be widely usable, across different types of blockchains and ledgers, even crossing international boundaries.
- Consent: subjects must consent to the use of their specified claims by other parties, whether interactive or not.
- Minimal disclosure: disclosure of private information involves the minimum amount necessary for the task at hand.
- Protection: freedoms and rights of the individual are preserved over the needs of the network when there is a conflict.
VCs are related to DIDs. From a high-level perspective, a DID concerns WHO the user is, whereas VCs concern WHAT the user can do. In this respect, DIDs and VC are orthogonal, but VCs are expected to use DIDs.
Within SOFIE we have designed solutions for incorporating these two technologies within the OAuth 2.0 authorization framework to provide secure and privacy preserving access to IoT systems. Furthermore, we have developed the appropriate protocol adapters so that legacy OAuth 2.0 clients and authorization servers can use SOFIE’s IAA and PDS components.
The proposed solution is lightweight enough to be used even by IoT gateways and constrained IoT devices, it prevents user tracking, and it enables revocation, accountability, and auditing solutions.
More information, including papers and presentations, related to the above topics that the Mobile Multimedia Laboratory at the Athens University of Economics and Business (AUEB) is investigating within the SOFIE project is available at https://mm.aueb.gr/blockchains.
- W3C Credentials Community Group. (2019) A primer for decentralized identifiers. [Online].
- Manu Sporny et al. (2019) Verifiable credentials data model 1.0. [Online].
- K. C. Toth and A. Anderson-Priddy, “Self-sovereign digital identity: A paradigm shift for identity,” IEEE Security Privacy, vol. 17, no. 3, pp. 17–27, May 2019